Data privacy and security
We've built our platform with robust security and compliance measures at its core. By meeting the highest standards for data management and security, Genomcore simplifies regulatory compliance and safeguards patient trust.
compliance & security
Genomcore makes compliance and security straightforward. Our features help healthcare, diagnostics, and biomedical companies overcome regulatory challenges while streamlining digital solution development.
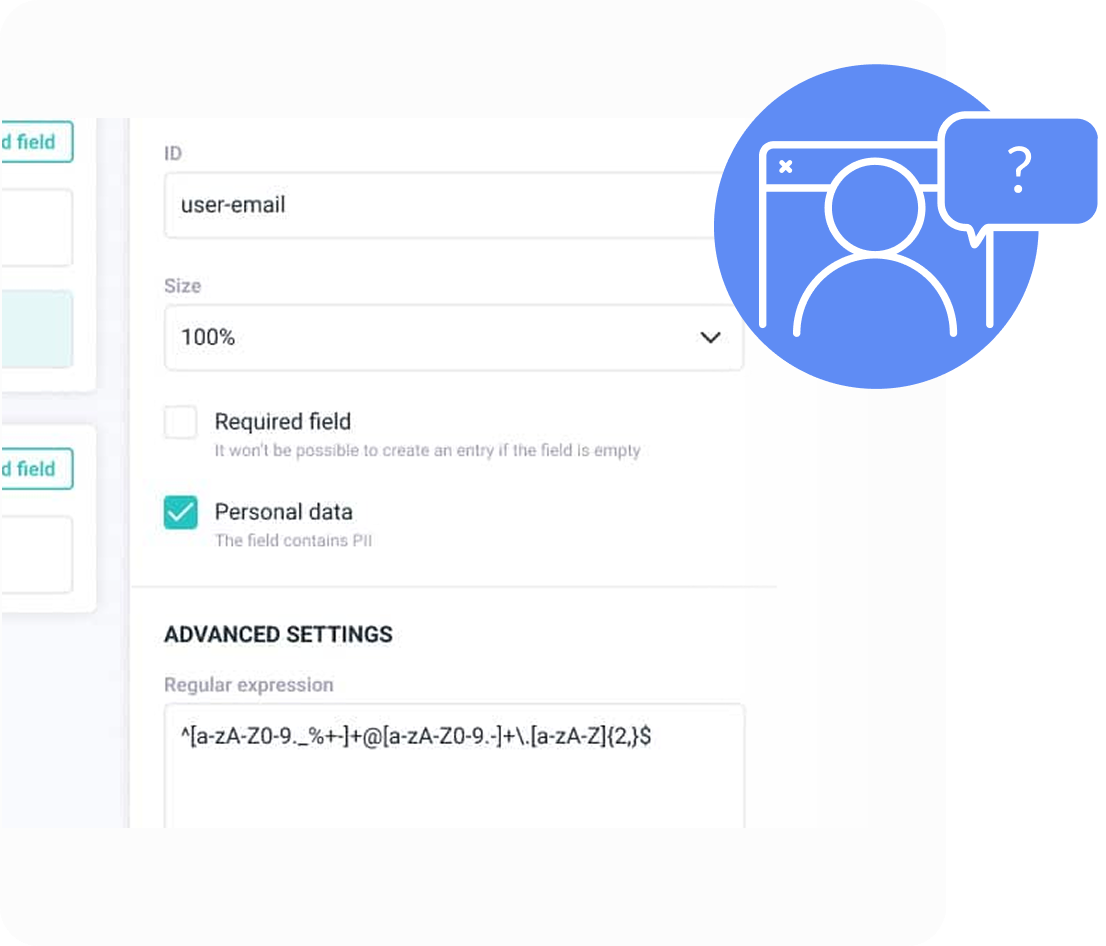
Manage Personal Identifiable Information (PII) with intuitive tools, designed to simplify compliance and protect sensitive data.
Each attribute or section within UMD Records can be flagged as a PII field. This makes data anonymization processes straightforward, and also allows for role-based pseudo-anonymization.
Many objects in the UMD can be linked to the legal owner of the information (such as a patient). This allows for built-in operations for data access, removal, or transfer.
Genomcore's technology streamlines the certification process for Software as Medical Device (SaMD - MDSW) for In Vitro Diagnostics (IVD), following ISO 13485 and IEC 62304 standards.
Turn your data science scripts and healthcare algorithms into compliant, certifiable software without complex coding or infrastructure setup.
Our team helps you prepare and complete the required technical documentation, ensuring your compliance journey is smooth and audit-ready.
From semantic modeling to full auditability and certifications, Genomcore is built with compliance in mind. We combine structured data governance, strong access control and global regulatory support under one unified platform.
Model and standardize data using ontologies and domain-specific templates
Define granular permissions and track usage with full audit logs
Ensure traceability and consistency across all workflows and modules
We've built our platform with robust security and compliance measures at its core. By meeting the highest standards for data management and security, Genomcore simplifies regulatory compliance and safeguards patient trust.
Information technology
Security techniques
Information security management systems
Requirements
Information technology
Security techniques
Code of practice for information security controls based on ISO/IEC 27002 for cloud services
Information technology
Security techniques
Code of practice for protection of personally identifiable information (PII) in public clouds acting as PII processors